💽
This is personal-use software without any warranties. If you use it for forensic assessments, ensure due diligence and check the formality requirements.
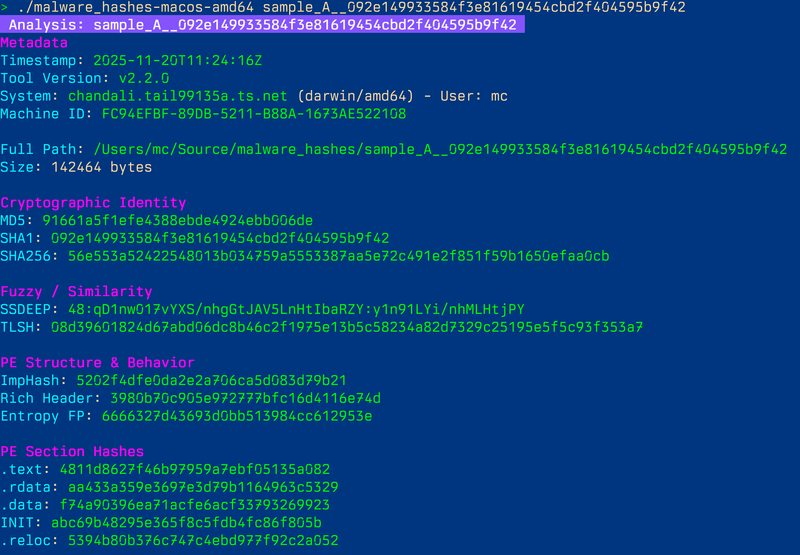
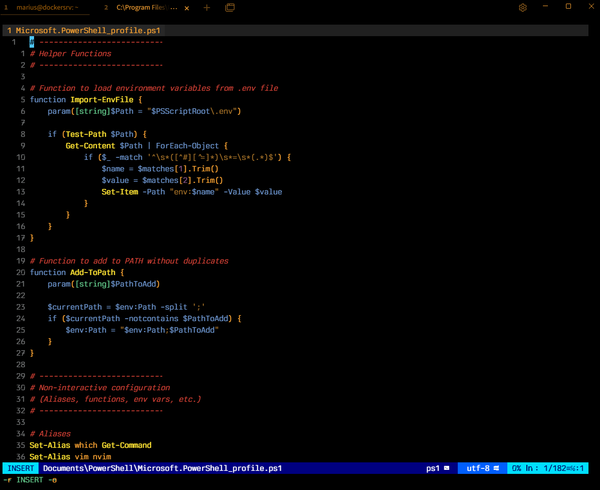
> xattr -d com.apple.quarantine malware_hashes-macos-amd64 > ./malware_hashes-macos-amd64 sample_A__092e149933584f3e81619454cbd2f404595b9f42 Analysis: sample_A__092e149933584f3e81619454cbd2f404595b9f42 Metadata Timestamp: 2025-11-20T11:24:16Z Tool Version: v2.2.0 System: chandali.tail99135a.ts.net (darwin/amd64) - User: mc Machine ID: FC94EFBF-89DB-5211-B88A-1673AE522108 Full Path: /Users/mc/Source/malware_hashes/sample_A__092e149933584f3e81619454cbd2f404595b9f42 Size: 142464 bytes Cryptographic Identity MD5: 91661a5f1efe4388ebde4924ebb006de SHA1: 092e149933584f3e81619454cbd2f404595b9f42 SHA256: 56e553a52422548013b034759a5553387aa5e72c491e2f851f59b1650efaa0cb Fuzzy / Similarity SSDEEP: 48:qD1nw017vYXS/nhgGtJAV5LnHtIbaRZY:y1n91LYi/nhMLHtjPY TLSH: 08d39601824d67abd06dc8b46c2f1975e13b5c58234a82d7329c25195e5f5c93f353a7 PE Structure & Behavior ImpHash: 5202f4dfe0da2e2a706ca5d083d79b21 Rich Header: 3980b70c905e972777bfc16d4116e74d Entropy FP: 6666327d43693d0bb513984cc612953e PE Section Hashes .text: 4811d8627f46b97959a7ebf05135a082 .rdata: aa433a359e3697e3d79b1164963c5329 .data: f74a90396ea71acfe6acf33793269923 INIT: abc69b48295e365f8c5fdb4fc86f805b .reloc: 5394b80b376c747c4ebd977f92c2a052
Quick notes
- Metadata contains a machine ID, which is generated either based on the Windows Registry or
- based on macOS
IOPlatformUUIDor - Linux (Dbus
machine-id)
- based on macOS
- MD5 is still used for many forensic archives
- Fuzzy hashes are useful to track malware families / variants
- PE structure is pretty standard
- no Mach-O or ELF support for now
The tool is written in Go and available for
- Windows (AMD64, ARM)
- macOS (AMD64, ARM)
- Linux (AMD64)
- source
GitHub - norandom/malware_hashes: Tool to hash malicious software for Malware Forensic reports (PERSONAL USE)
Tool to hash malicious software for Malware Forensic reports (PERSONAL USE) - norandom/malware_hashes